Session 2, HTTP Traffic Analysis & Flood Simulation (LAB ONLY)
Objective: Run a simple HTTP server in Kali, capture HTTP traffic in Windows, and distinguish normal patterns from an ICMP flood.LAB ONLY: Flood only in Host-Only/isolated network....
Objective: Run a simple HTTP server in Kali, capture HTTP traffic in Windows, and distinguish normal patterns from an ICMP flood.LAB ONLY: Flood only in Host-Only/isolated network....

Objective: Run a simple HTTP server in Kali, capture HTTP traffic in Windows, and distinguish normal patterns from an ICMP flood.
LAB ONLY: Flood only in Host-Only/isolated network.
Prerequisites & Topology Same topology as Session 1. Kali = HTTP server 10.37.129.3, Windows = client 10.37.129.2.
Preparation Kali has Python 3:

Windows/Mac os is ready to run Wireshark.
Steps
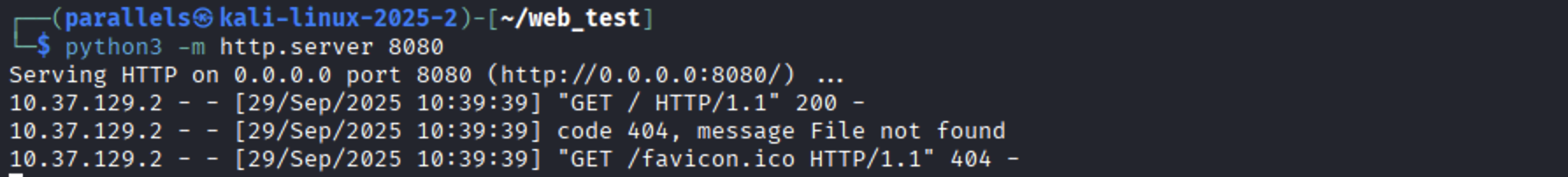
Windows (PowerShell/Browser)/ Mac os (Terminal):
powershell/terminal

# or open in browser
Wireshark display filter:
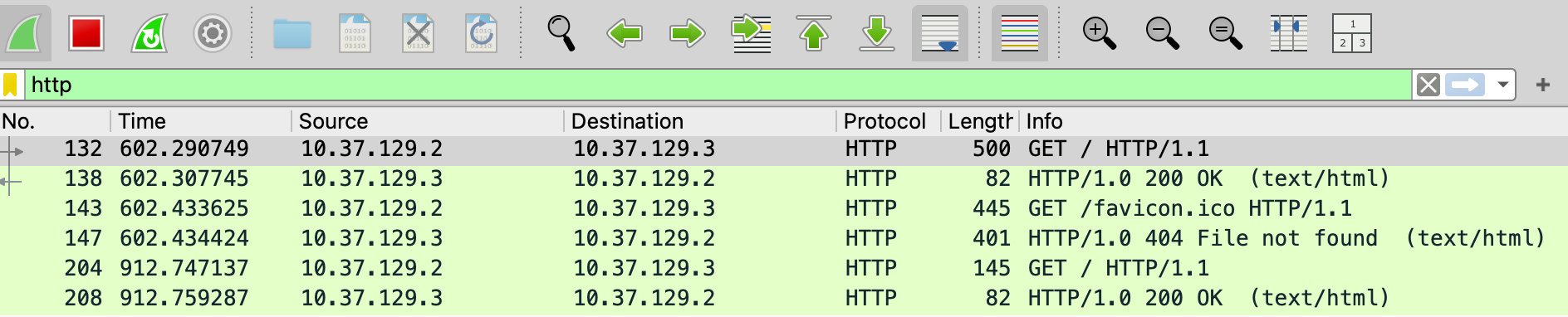
Check: GET / HTTP/1.1, 200 OK, headers (Host, User-Agent, Content-Type).
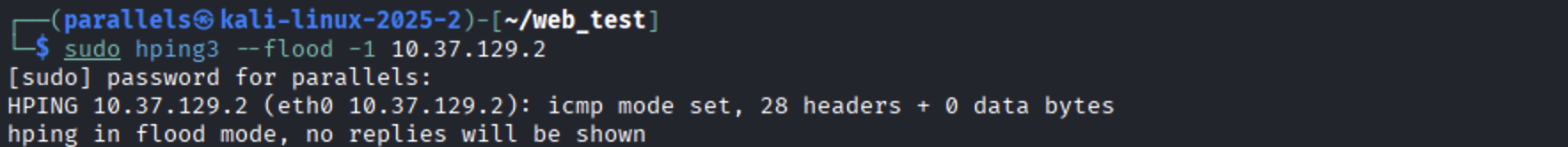
alternative (lighter):

Wireshark: stop after a few seconds → Statistics → I/O Graph; compare pps before/during flood. Filter: icmp.
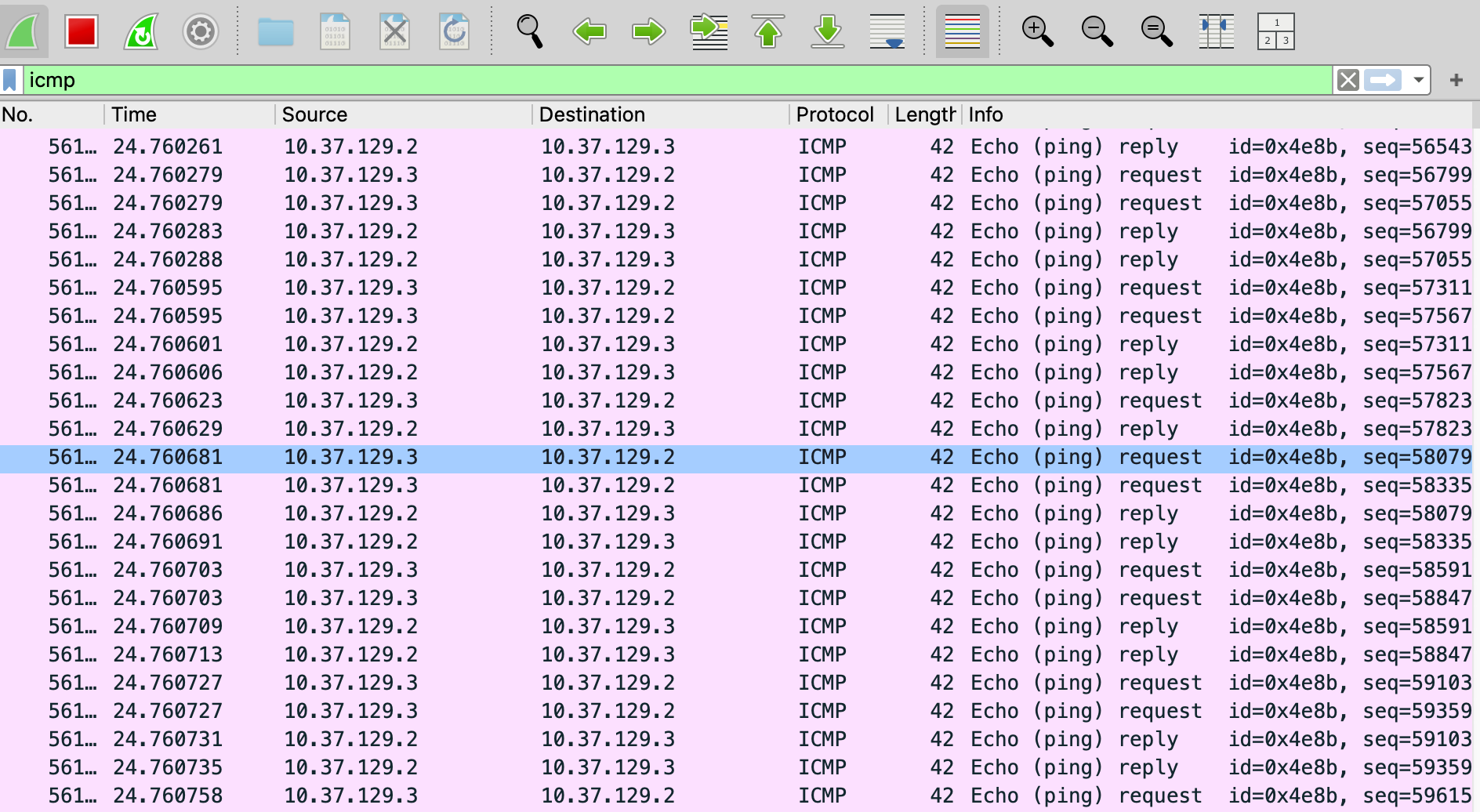
Verification / Results
Cleanup
Troubleshooting
Tinggalkan komentar dengan namamu dan kami akan menampilkannya di sini.
Jadilah yang pertama memberikan komentar pada tulisan ini.
Fresh insights and tutorials handpicked for your curiosity.
1. Switch to the Root UserFirst, switch to the root user to ensure you have full administrative privileges:sud...
Read articleObjective: Set up VM topology, ensure bidirectional connectivity, and perform ICMP packet capture & analys...
Read articleAlgoritma evolusioner (Evolutionary Algorithms, EA) adalah kelompok metode optimasi yang terinspirasi dari pro...
Read article🤖 Apa Itu Machine Learning?Machine learning (ML) adalah cabang dari kecerdasan buatan (AI) yang memungkinkan...
Read article