Snort IDS Setup and Testing Tutorial
1. Switch to the Root UserFirst, switch to the root user to ensure you have full administrative privileges:sudo su2. Update Your SystemEnsure your package lists are up to date. Fir...

1. Switch to the Root UserFirst, switch to the root user to ensure you have full administrative privileges:sudo su2. Update Your SystemEnsure your package lists are up to date. Fir...

First, switch to the root user to ensure you have full administrative privileges:
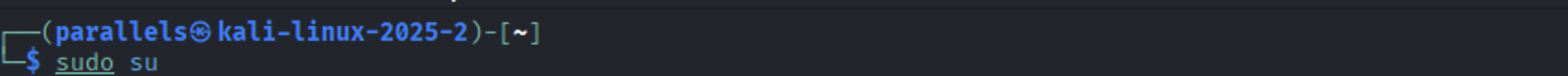
Ensure your package lists are up to date. First, do an import and save the GPG (GNU Privacy Guard) key from the Kali Linux repository into the system:
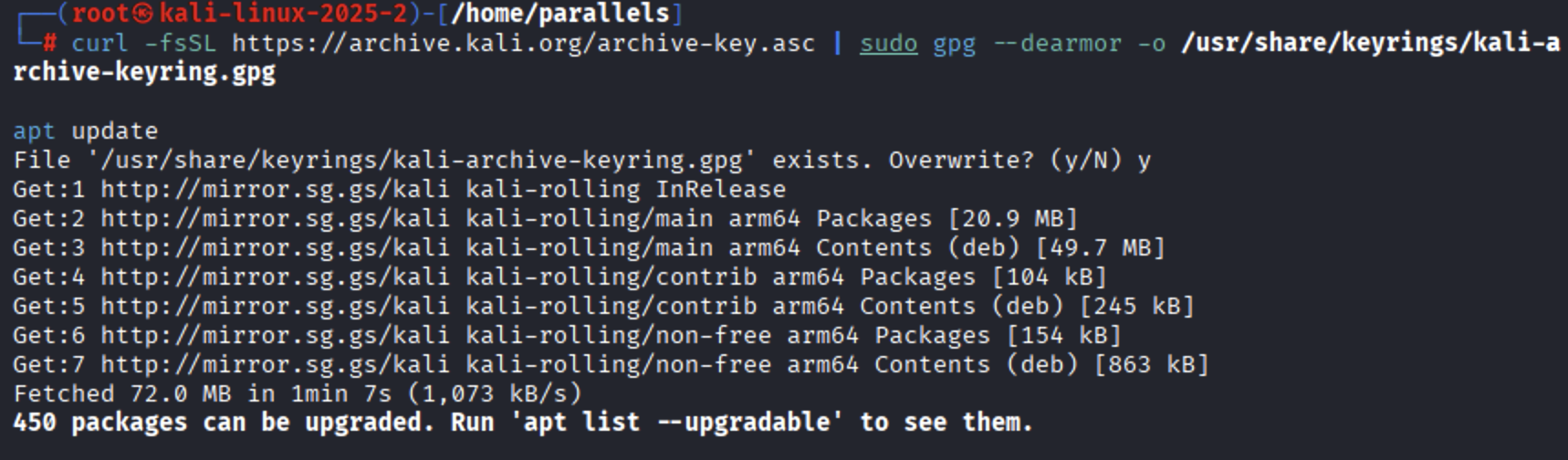
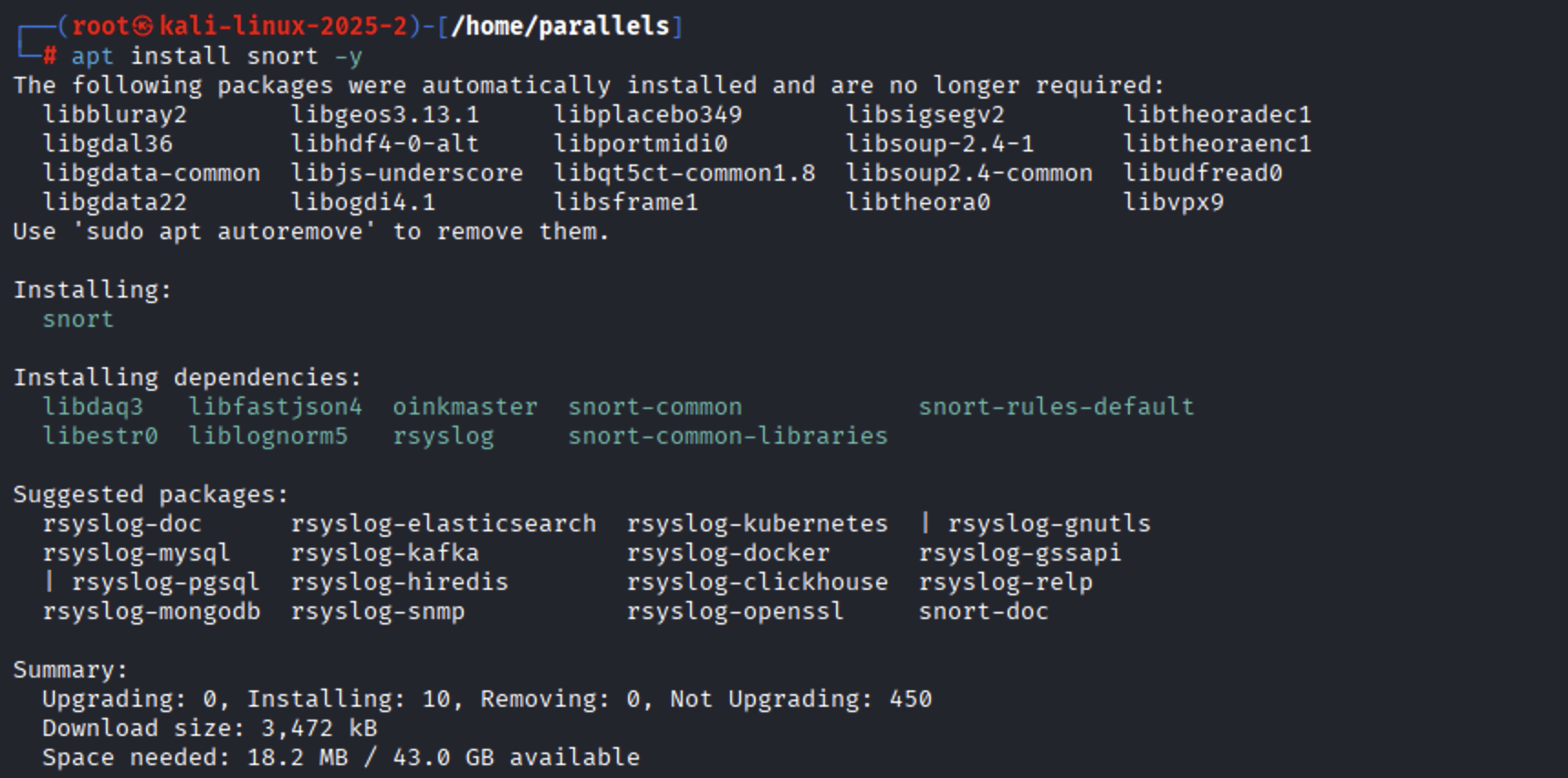
Install the Snort package:
Verify the installation by checking the Snort version:
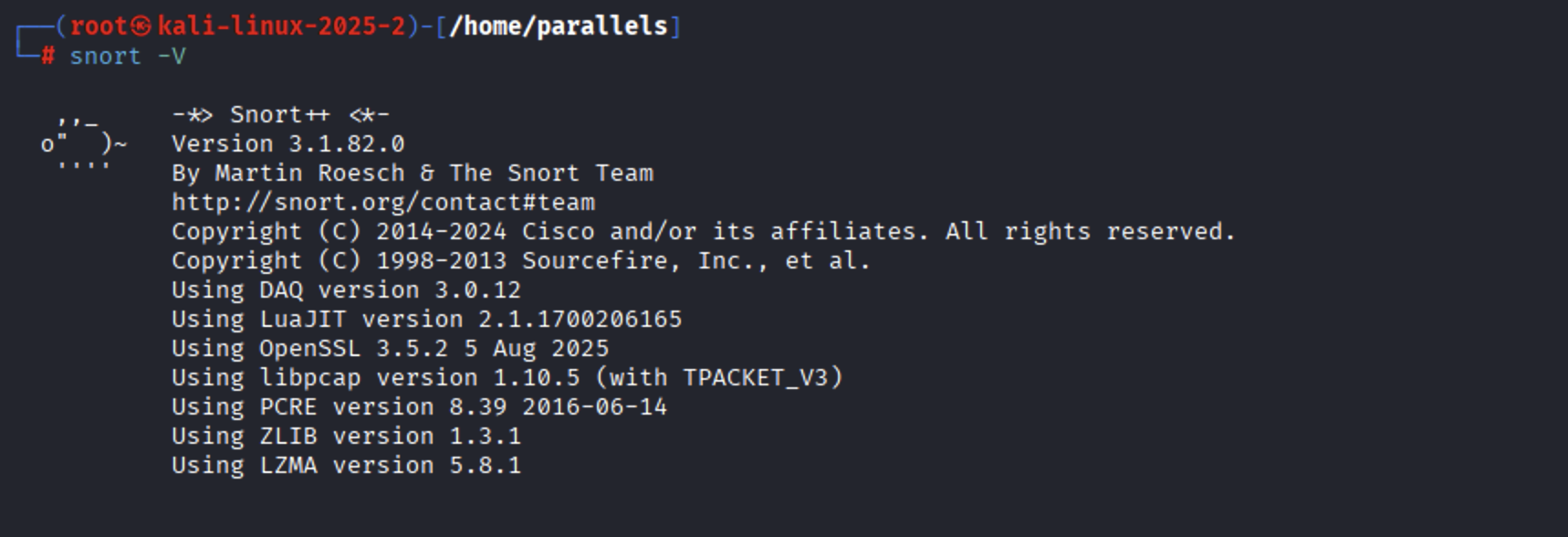
You should see the Snort version and build information if the installation was successful.
Change to the directory where Snort configuration files are stored:

List the contents of this directory to see the configuration files:
Edit the main Snort configuration file:

Add the following configuration block for IPS:
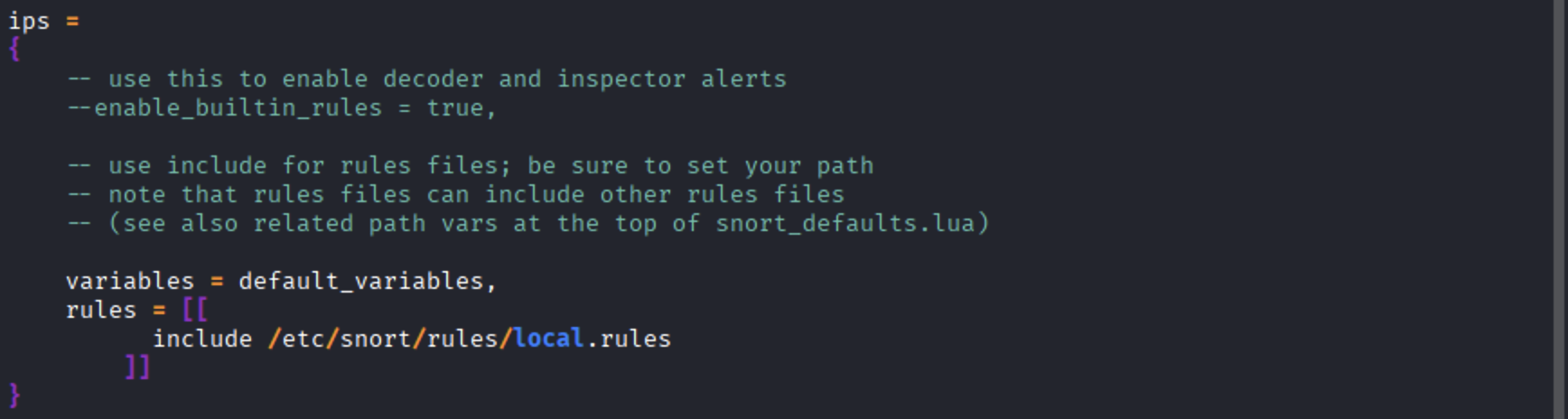
Save the file and exit the editor (Ctrl + O, Enter, then Ctrl + X).
Create or edit the local.rules file where your custom detection rules will be stored:

Add the following rules to detect common scanning techniques (make sure each rule is set in one line):
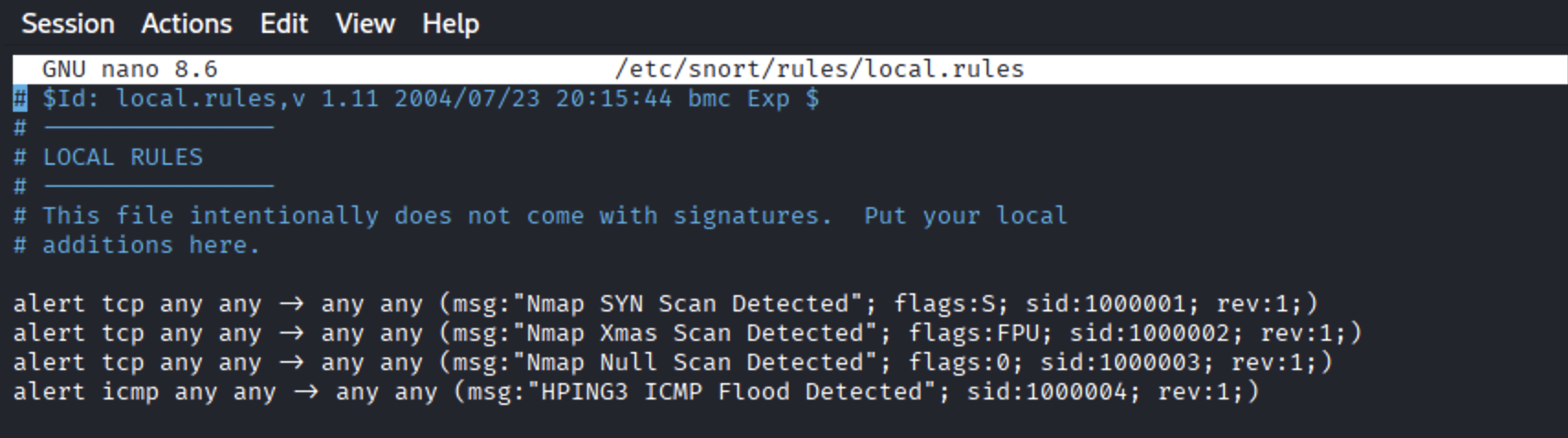
Save the file and exit (Ctrl + O, Enter, then Ctrl + X).
Start Snort to monitor a specific network interface:
For external interface (e.g., eth0):
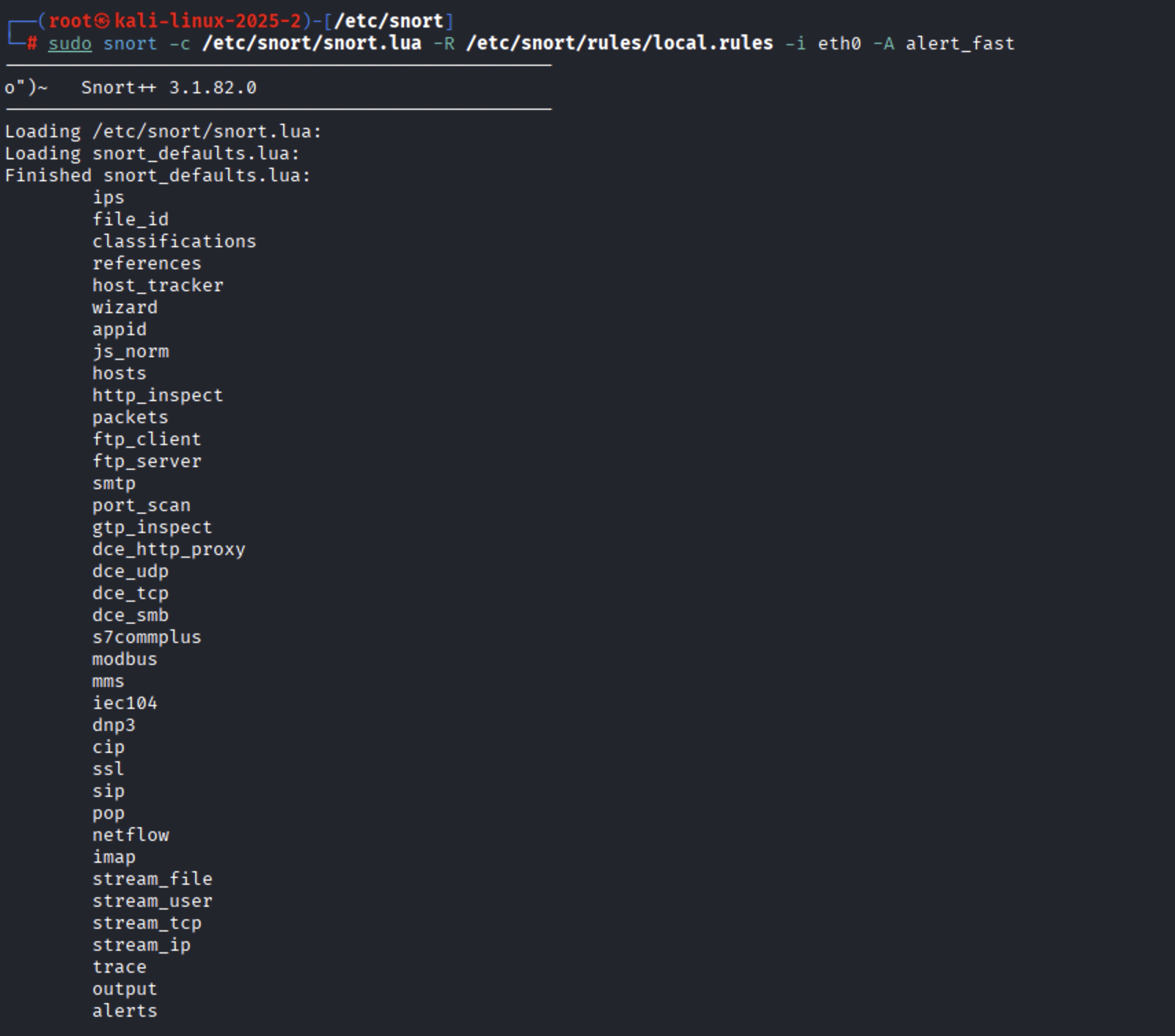
For the loopback interface (lo):
Run some common scanning attacks to test your Snort configuration:
Nmap Scans:
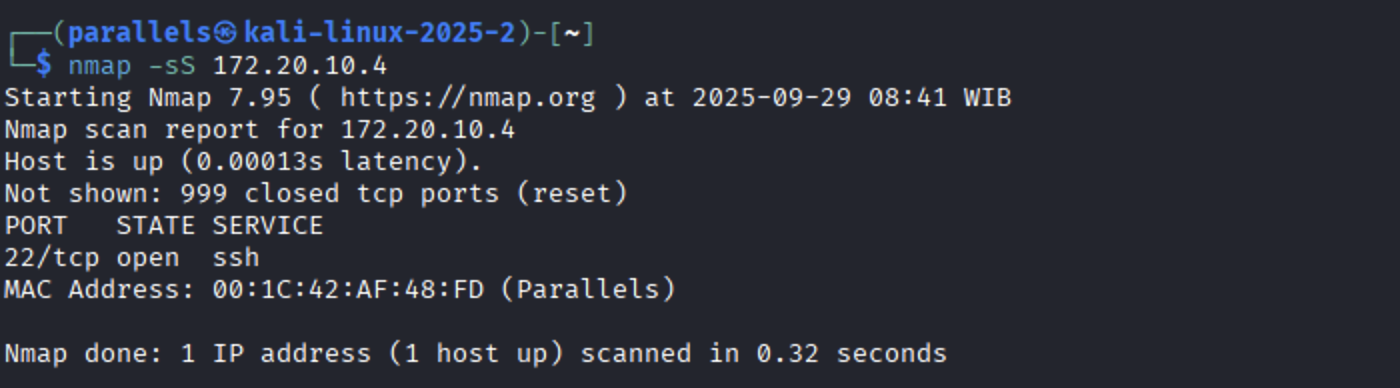
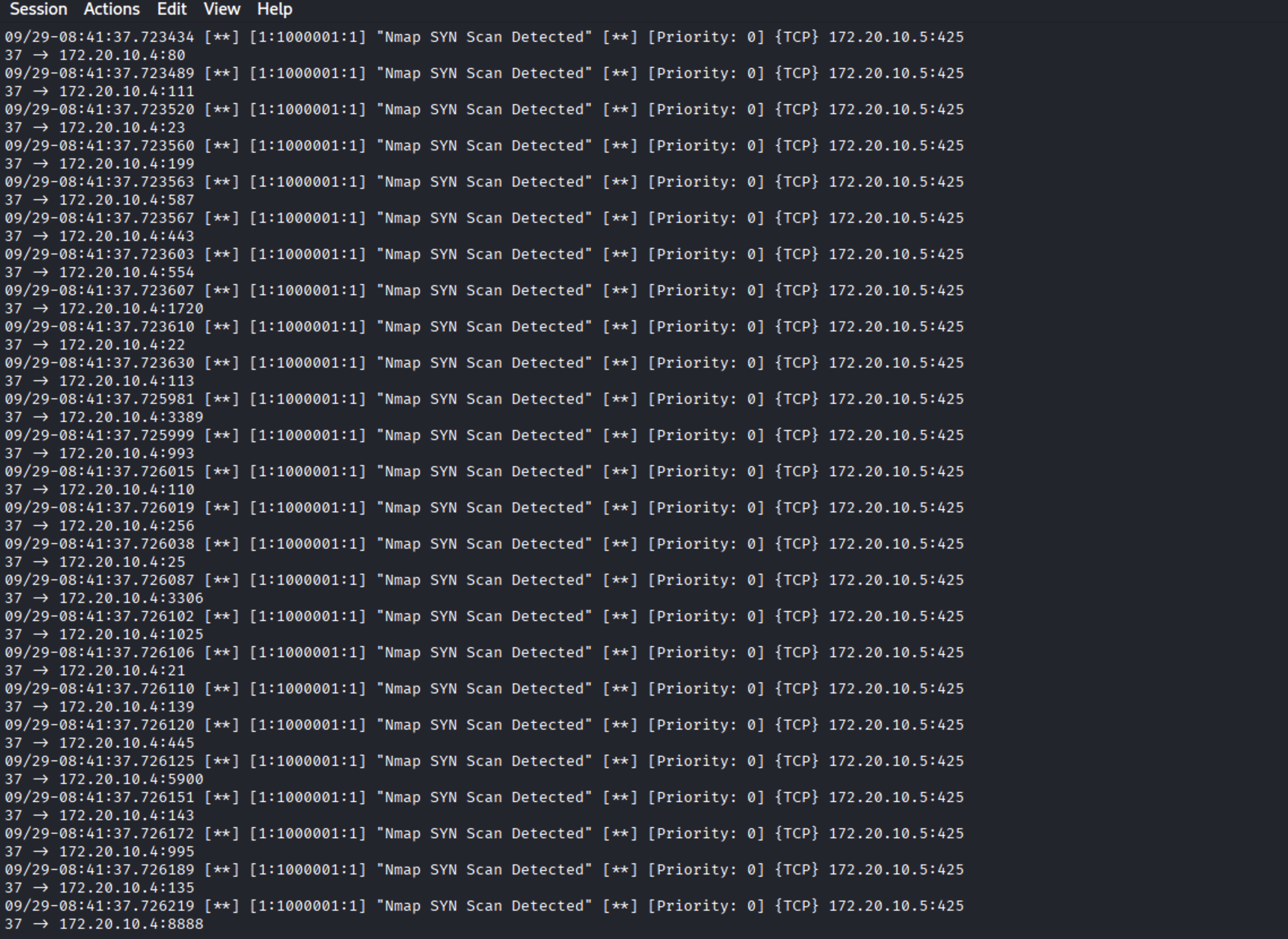
ICMP Flood with hping3:
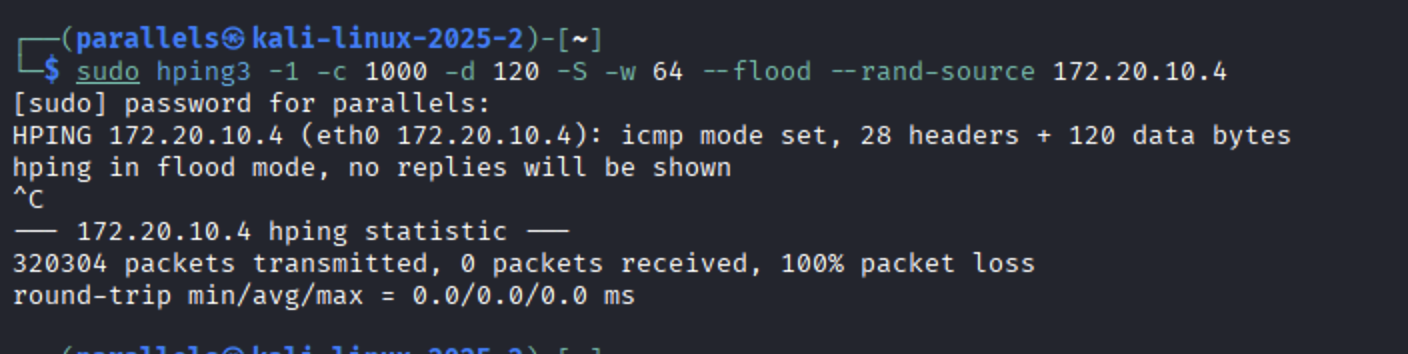
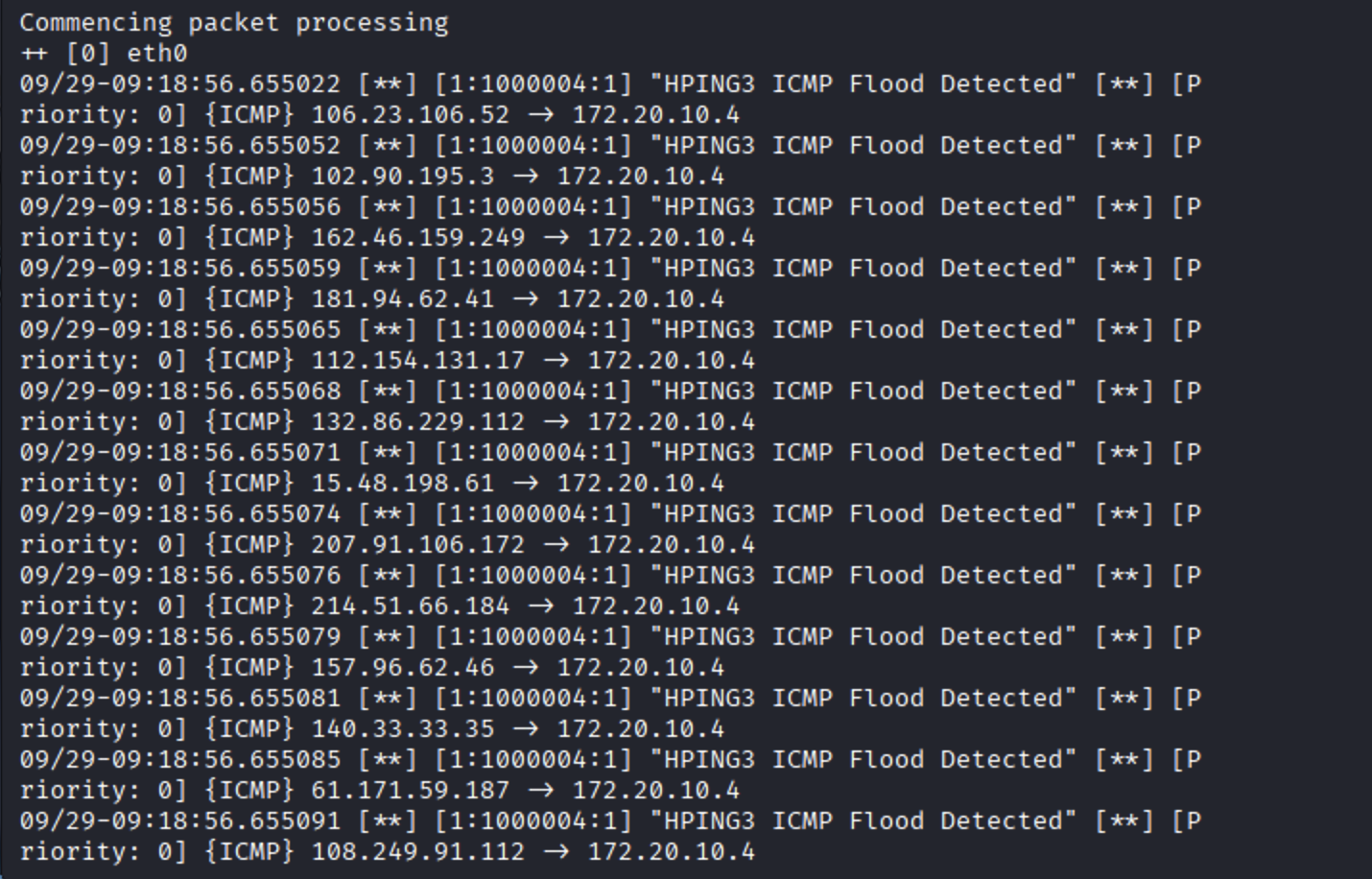
If the rules are correctly configured, you should see alerts in the Snort console.
To make Snort start automatically on boot, create a systemd service file:

Add the following content:
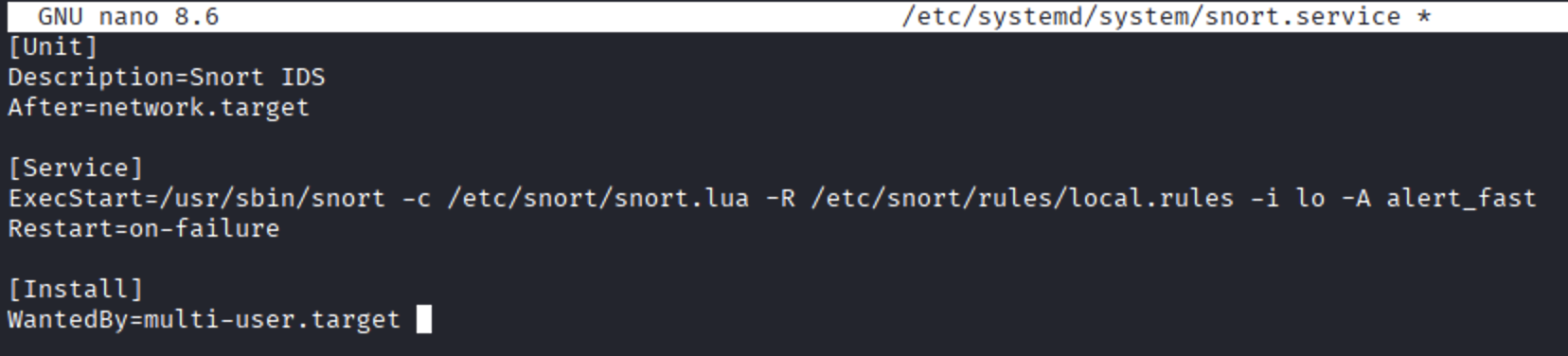
Save and exit (Ctrl + O, Enter, then Ctrl + X).
Reload the systemd daemon to recognize the new service:
Enable Snort to start on boot:
Start the Snort service:
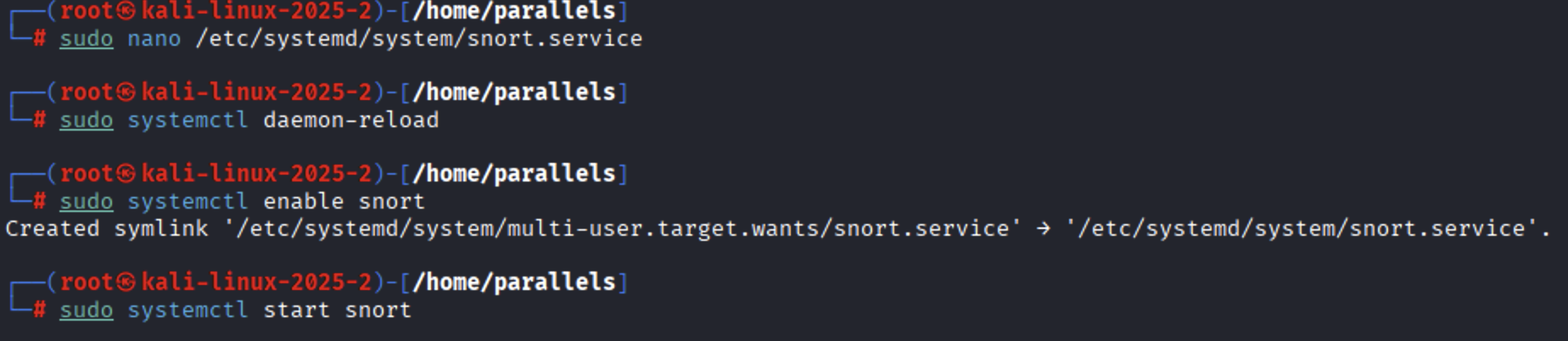
To stop the Snort service:
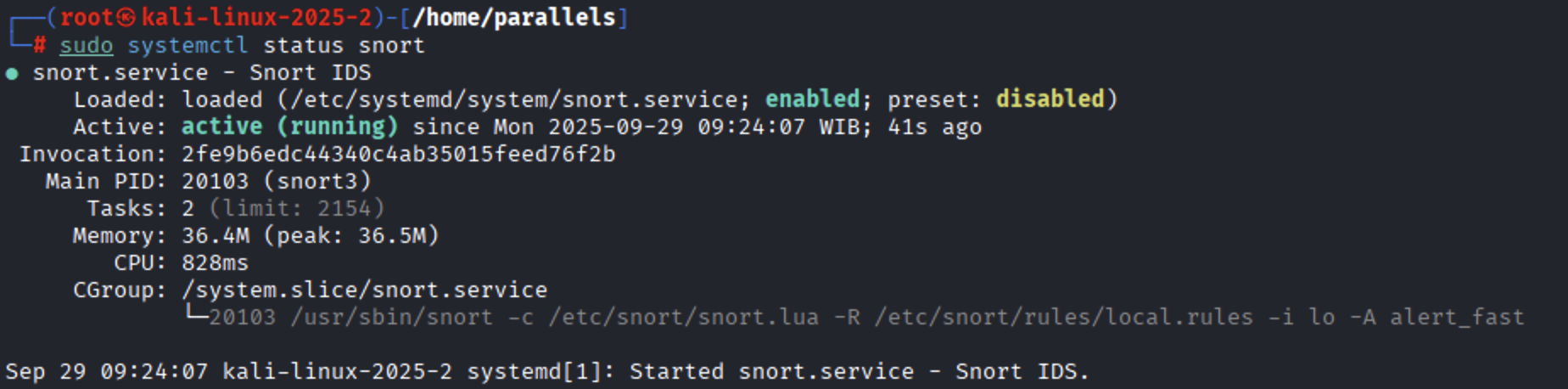
Check the status of the Snort service:
Tinggalkan komentar dengan namamu dan kami akan menampilkannya di sini.
Jadilah yang pertama memberikan komentar pada tulisan ini.
Fresh insights and tutorials handpicked for your curiosity.
Objective: Run a simple HTTP server in Kali, capture HTTP traffic in Windows, and distinguish normal patterns...
Read articleObjective: Set up VM topology, ensure bidirectional connectivity, and perform ICMP packet capture & analys...
Read articleAlgoritma evolusioner (Evolutionary Algorithms, EA) adalah kelompok metode optimasi yang terinspirasi dari pro...
Read article🤖 Apa Itu Machine Learning?Machine learning (ML) adalah cabang dari kecerdasan buatan (AI) yang memungkinkan...
Read article